This unique address is called the IP address. Nagios is an open source monitoring system for computer systems.

Top 10 Best Practices For Network Monitoring In 2022 Toolbox Tech
OpManager Plus starts its service life by scanning the network and creating a topology map and device inventory.

. Standardization or standardisation is the process of implementing and developing technical standards based on the consensus of different parties that include firms users interest groups standards organizations and governments. Then looks at how bandwidth utilization monitors network analysis systems and packet sniffers work and how. Top 10 Intrusion Detection Tools is a review of the top 10 intrusion detection tools.
This includes network device health monitoring and traffic flow analysis utilities. SolarWinds Server Application Monitor FREE TRIAL. What is the IP Address.
In the server-side Storage Logging log the server request ID appears the Request ID header column. For example emit information in a self-describing format such as JSON MessagePack or Protobuf rather than ETLETW. In other words every device on a network has a unique address that helps with its identification.
Standardization can help maximize compatibility interoperability safety repeatability or qualityIt can also facilitate a normalization of formerly. Using a standard format enables the system to construct processing pipelines. In a network trace such as one captured by Fiddler the server request ID appears in response messages as the x-ms-request-id HTTP header value.
We looked at components of the Orion suite in our article on the best sFlow traffic analyzersWhere the Server Health Monitor can meet the needs of a small shop SAM. Top 15 Network Monitoring Tools Reviewed starts by discussing the need for network monitoring tools and the different types of tools that are available. Server request ID.
Internet Protocol IP address is a set of numbers that play a two-pronged role in a network one to identify a device uniquely and the other to identify its location. That gives you an overview of your network and then you can work on testing the traffic on each link or end to end between two nodes on the network. In the client-side log that the Storage.
It was designed with core components to run on the Linux operating system and can monitor devices running Linux Windows and Unix OSes. The storage service automatically generates server request IDs. All output from the monitoring agent or data-collection service should be an agnostic format thats independent of the machine operating system or network protocol.
The SolarWinds Server.

8 Best Bandwidth Monitoring Tools For 2022 Network Traffic Usage
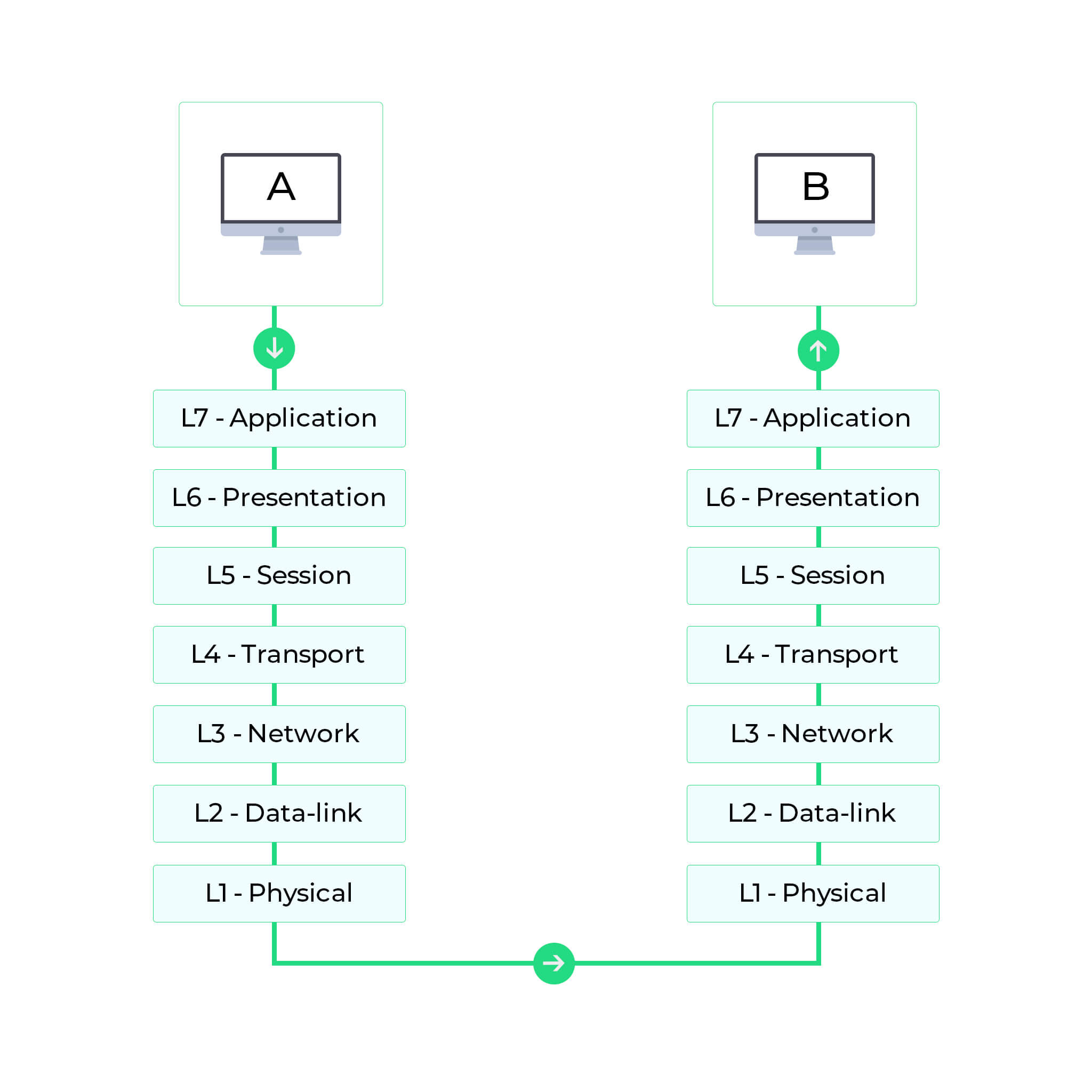
Network Protocols Types Of Networking Protocols Manageengine Opmanager

Top 10 Best Practices For Network Monitoring In 2022 Toolbox Tech
0 Comments